Decoding the Renaissance exhibition material: Difference between revisions
(Reformatted page to match earlier exhibition pages. Removed dates by names. Added "Call number" in front of Folger items. More Hamnet/LUNA links are at http://old.folger.edu/Content/Whats-On/Folger-Exhibitions/Decoding-the-Renaissance/Item-List.cfm) |
SophieByvik (talk | contribs) (added images) |
||
| (19 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
This article offers a comprehensive and descriptive list of each piece included in the [[Decoding the Renaissance: 500 Years of Codes and Ciphers|''Decoding the Renaissance: 500 Years of Codes and Ciphers'']], one of the [[Exhibitions at the Folger]]. | This article offers a comprehensive and descriptive list of each piece included in the [[Decoding the Renaissance: 500 Years of Codes and Ciphers|''Decoding the Renaissance: 500 Years of Codes and Ciphers'']], one of the [[Exhibitions at the Folger]]. | ||
This exhibition was arranged into three | This exhibition was arranged into three zones: [[#The Renaissance of Cryptography (zone 1)|The Renaissance of Cryptography]]; [[#How To Make Anything Signify Anything (zone 2)|How To Make Anything Signify Anything]]; and [[#Enigmas and Machines (zone 3)|Enigmas and Machines]]. | ||
__NOTOC__ | __NOTOC__ | ||
== The Renaissance of Cryptography == | == The Renaissance of Cryptography (zone 1)== | ||
[[File:X.c.125 pg.1.jpg|thumb|right|260px|Coded letter for Charles I from from George Digby, Oxford, to Prince Rupert or Prince Maurice, 1645. Folger Digital Image [http://luna.folger.edu/luna/servlet/s/glc3dv 5761].]] | |||
:''...a familiarity with the conditions and customs of [the sixteenth and seventeenth centuries] will bring one to the conclusion that there were, indeed, very few things in those days that did not have something to do with ciphers. '' | :''...a familiarity with the conditions and customs of [the sixteenth and seventeenth centuries] will bring one to the conclusion that there were, indeed, very few things in those days that did not have something to do with ciphers. '' | ||
::—William F. Friedman, "Saying it in Cipher" (1920) | ::—William F. Friedman, "Saying it in Cipher" (1920) | ||
| Line 12: | Line 12: | ||
The Renaissance was the first great age of mass communication, but it was also the period when the art of secret writing came into its own. The new science of codes and ciphers produced some of the period’s most brilliant inventions, most beautiful books, and most enduring legacies. | The Renaissance was the first great age of mass communication, but it was also the period when the art of secret writing came into its own. The new science of codes and ciphers produced some of the period’s most brilliant inventions, most beautiful books, and most enduring legacies. | ||
One of the oldest cryptographic books was written by the quintessential Renaissance Man, Leon Battista Alberti. His short text on ciphers, Opuscoli morali, first published in this 1568 collection, was written a century earlier, making it Europe’s oldest extant treatise on ciphers and earning Alberti the title of Father of Western Cryptology. | One of the oldest cryptographic books was written by the quintessential Renaissance Man, Leon Battista Alberti. His short text on ciphers, ''Opuscoli morali'', first published in this 1568 collection, was written a century earlier, making it Europe’s oldest extant treatise on ciphers and earning Alberti the title of Father of Western Cryptology. | ||
However, the first printed cryptographic book was Trithemius’ posthumous work on polygraphic (or multiple writing) systems, Polygraphiae libri sex. The title -page | However, the first ''printed'' cryptographic book was Trithemius’ posthumous work on polygraphic (or multiple writing) systems, ''Polygraphiae libri sex''. The title-page depicts Trithemius presenting the book to its dedicatee, Emperor Maximilian I. The monk behind him provides the keys to the locked book, whose secrets are central to the exercise of power in church and state. | ||
==== Items Included ==== | ==== Items Included ==== | ||
* Leon Battista Alberti. ''Opuscoli morali''. Venice: Francesco di Franceschi, 1568. Call number: PQ4562 .A6 1568 Cage; displayed A1v | * Leon Battista Alberti. ''Opuscoli morali''. Venice: Francesco di Franceschi, 1568. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=110610 PQ4562 .A6 1568 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/xpl3o2 sig. A1v] and [http://luna.folger.edu/luna/servlet/s/7r3w30 LUNA Digital Image]. | ||
* Johannes Trithemius. ''Polygraphiae libri sex''. [Basel]: Johann Haselberg, 1518. Call number: | * Johannes Trithemius. ''Polygraphiae libri sex''. [Basel?]: Johann Haselberg, 1518. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=263020 Folio Z103.T7 P6 1518 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/cu8z87 title page]. | ||
=== The First Cryptographic Couple (case 2 and wall panel)=== | === The First Cryptographic Couple (case 2 and wall panel)=== | ||
William Frederick Friedman (1891–1969) and Elizebeth Smith Friedman (1892–1980) are sometimes described as the nation's First Cryptographic Couple. They were introduced to the subject and to each other by the larger-than-life textile magnate George Fabyan at Riverbank, a country estate and research institute near Chicago. They joined a team providing support for Elizabeth Wells Gallup, the leading advocate of the popular idea that Francis Bacon had written Shakespeare's works and left ciphered clues throughout the 1623 First Folio and other texts. The Friedmans quickly lost faith in this theory and moved to Washington, where William ran the Signals Intelligence Service and Elizebeth worked for the Coast Guard and other agencies. But they continued their study of the Renaissance and eventually settled on Capitol Hill. Many of the books they used at Riverbank are now housed across the street in the Fabyan Collection at the Library of Congress. | William Frederick Friedman (1891–1969) and Elizebeth Smith Friedman (1892–1980) are sometimes described as the nation's First Cryptographic Couple. They were introduced to the subject and to each other by the larger-than-life textile magnate George Fabyan at Riverbank, a country estate and research institute near Chicago. They joined a team providing support for Elizabeth Wells Gallup, the leading advocate of the popular idea that Francis Bacon had written Shakespeare's works and left ciphered clues throughout the 1623 First Folio and other texts. The Friedmans quickly lost faith in this theory and moved to Washington, where William ran the Signals Intelligence Service and Elizebeth worked for the Coast Guard and other agencies. But they continued their study of the Renaissance and eventually settled on Capitol Hill. Many of the books they used at Riverbank are now housed across the street in the Fabyan Collection at the Library of Congress. | ||
==== The Friedmans and Shakespeare ==== | |||
After leaving Riverbank in 1920, the Friedmans remained in close contact with Elizabeth Wells Gallup and her fellow Baconians, collecting materials for this comprehensive critique of the Baconian authorship theory. By the late 1940s, they were giving lectures called “The Cryptologist Looks at Shakespeare.” Their original typescript (bearing that earlier title) was finished in 1954 and the revised book was published to great acclaim three years later by Cambridge University Press. | |||
==== Items Included ==== | ==== Items Included ==== | ||
| Line 29: | Line 33: | ||
===== Case 2 ===== | ===== Case 2 ===== | ||
* LOAN courtesy of the Library of Congress. William F. Friedman. ''Methods for the Solutions of Ciphers''. Geneva, Ill.: Riverbank Laboratories, 1917–22. | * LOAN courtesy of the [http://loc.gov Library of Congress]. William F. Friedman. ''Methods for the Solutions of Ciphers''. Geneva, Ill.: Riverbank Laboratories, 1917–22. | ||
* LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Exceptional Civilian Service Medal. Presented to William F. Friedman in 1944. | * LOAN courtesy of the [http://marshallfoundation.org/library/collection/subject-guides/code-breaking-subject-guide/#!/collection=926 George C. Marshall Foundation], Lexington, VA. Exceptional Civilian Service Medal. Presented to William F. Friedman in 1944. | ||
* LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Medal for Merit. Presented to William F. Friedman in 1946. | * LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Medal for Merit. Presented to William F. Friedman in 1946. | ||
* William F. Friedman and Elizebeth S. Friedman. ''The Shakespearean Ciphers Examined''. Cambridge: Cambridge University Press, 1957. | * William F. Friedman and Elizebeth S. Friedman. ''The Shakespearean Ciphers Examined''. Cambridge: Cambridge University Press, 1957. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=52477 PR2937 .F7 1957 Copy 2 Cage] and [http://luna.folger.edu/luna/servlet/s/y6j081 LUNA Digital Image]. | ||
* LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Photo of William F. Friedman and Elizebeth S. Friedman, ca. 1957. 310 2nd Street SE, Washington, DC. | * LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Photo of William F. Friedman and Elizebeth S. Friedman, ca. 1957. 310 2nd Street SE, Washington, DC. | ||
===== Wall Panel ===== | ===== Wall Panel ===== | ||
* LOAN courtesy of the Bacon cipher collection, | * LOAN courtesy of the [http://archives.nypl.org/mss/176#descriptive_identity Bacon cipher collection, 1893–1948]. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox, and Tilden Foundations. William F. Friedman. ''Cipher Baconis Gallup''. Manuscript, ca. March 1916. NYPL Call number: [http://catalog.nypl.org/record=b11628269~S1 MssCol 176]. | ||
=== Invisible Ink (case 3) === | === Invisible Ink (case 3) === | ||
Not all secret communication depends on codes and ciphers, and one of the oldest tricks in the book was to make the message itself invisible. Using nothing more than materials found in the average | Not all secret communication depends on codes and ciphers, and one of the oldest tricks in the book was to make the message itself invisible. Using nothing more than materials found in the average kitchen—[https://youtu.be/x_cKUqH10Nc lemon juice and a candle]—it is possible to make written letters disappear and reappear at will. | ||
==== Items Included ==== | ==== Items Included ==== | ||
* John Wilkins.. ''Mercury; or the secret and swift messenger''. London: J. Norton for John Maynard and Timothy Wilkins, 1641. Call number: W2202; displayed | * John Wilkins.. ''Mercury; or the secret and swift messenger''. London: J. Norton for John Maynard and Timothy Wilkins, 1641. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=136370 W2202]; displayed [http://luna.folger.edu/luna/servlet/s/7khk08 p. 42–43]. | ||
* Miscellaneous collection of recipes. Manuscript, ca. 1600. V.a.140; displayed | * Miscellaneous collection of recipes. Manuscript, ca. 1600. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=231384 V.a.140]; displayed [http://luna.folger.edu/luna/servlet/s/ffdc55 fol. 14v]. | ||
* LOAN courtesy of the Library of Congress. H. O. Nolan. ''The Production and Detection of Messages in Concealed Writing and Images''. Geneva, Ill.: Riverbank Laboratories, 1918. | * LOAN courtesy of the Library of Congress. H. O. Nolan. ''The Production and Detection of Messages in Concealed Writing and Images''. Geneva, Ill.: Riverbank Laboratories, 1918. LOC Call number: [http://lccn.loc.gov/96125614 Z104.5 .N65 1918b]. | ||
=== Secretaries, Scribes, and Ciphers (case 4 and wall panel) === | === Secretaries, Scribes, and Ciphers (case 4 and wall panel) === | ||
[[File:245- 323f back endleaf 3r.jpg|thumb|right|240px|''De historia stirpium'', 1542. Folger Digital Image [http://luna.folger.edu/luna/servlet/s/3n1hai 84205].]] | |||
The cryptographic book emerged with—and through—the invention of moveable type, but people had been using cryptographic means to secure their communications for centuries before the advent of print. Diplomatic and commercial business throughout the Medieval and Early Modern periods depended heavily on handwritten codes and ciphers: official correspondence and private documents alike are peppered with mysterious symbols designed to be read only by those who had the key to the system. | |||
==== Sir Francis Walsingham ==== | |||
Widely known and feared as England's first spymaster, Secretary of State Sir Francis Walsingham used every trick in the book to search out secrets among his enemies while keeping his own communications secure. In the letter to the right of this text, he communicates Queen Elizabeth's wishes as the King of France was on his deathbed: he advises "great circumspection" in "the matter" and urges those involved to "beware whom they trust." He is careful to put the most sensitive information into cipher. You can see one of his ciphered letters on the right. | |||
==== Sir Francis Bacon ==== | |||
In addition to leaving secret codes in Shakespeare's plays (a theory that has proven unfounded), famous politician Sir Francis Bacon is known for providing the first English summary of the science of ciphers in his famous work ''Of the Advancement of Learning''. In this text, he describes his own invention—"while just a teenager"—of the so-called [[#Bacon's Biliteral Cipher (case 9)|biliteral cipher]]. The original 1605 edition mentions the episode only in passing; but the extended Latin edition of 1623 and its English version of 1640 explain the system in detail and show how it works in practice. | |||
==== Items Included ==== | ==== Items Included ==== | ||
===== Case 4 ===== | ===== Case 4 ===== | ||
* Sir Francis Walsingham. Autograph letter, partly in cipher, to unknown recipient, May 26, 1574. Manuscript compilation, 17th or 18th century. Call number: V.b.264; displayed | * Sir Francis Walsingham. Autograph letter, partly in cipher, to unknown recipient, May 26, 1574. Manuscript compilation, 17th or 18th century. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=224584 V.b.264, before p. 435]; displayed [http://luna.folger.edu/luna/servlet/s/q6hp33 item 5 btwn. p. 434–435]. | ||
* Leonhart Fuchs. ''De historia stirpium''. Basel: Michael Isingrin, 1542. Call number: 245- 323f; displayed back endleaf | * Leonhart Fuchs. ''De historia stirpium commentarij insignes maximis impensis et uigilijs elaborati''. Basel: Michael Isingrin, 1542. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=124560 245- 323f]; displayed [http://luna.folger.edu/luna/servlet/s/hmu80s back endleaf 3r] and [http://luna.folger.edu/luna/servlet/s/yfcu3h LUNA Digital Image]. | ||
===== Wall Panel ===== | ===== Wall Panel ===== | ||
* George Digby, | * George Digby. Autograph letter signed from George Digby, Oxford, to Prince Rupert or Prince Maurice. Coded letter written for King Charles I. 27 April 1645. Call number [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=184910 X.c.125]; displayed [http://luna.folger.edu/luna/servlet/s/e0qc16 p. 1] and [http://luna.folger.edu/luna/servlet/s/c6yy59 LUNA Digital Image]. | ||
=== The Secret Science at a Glance (case 5) === | === The Secret Science at a Glance (case 5) === | ||
| Line 69: | Line 81: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* LOAN courtesy of the Library of Congress. Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. ''Cryptomenytices et cryptographiae libri IX''. Lüneburg: Johann and Heinrich Stem, 1624. | * LOAN courtesy of the Library of Congress. Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. ''Cryptomenytices et cryptographiae libri IX''. Lüneburg: Johann and Heinrich Stem, 1624. LOC Call number: [http://lccn.loc.gov/03019229 Z103 .A95]. | ||
* LOAN courtesy of the Library of Congress. Claude Comiers. ''Traité de la parole, langues, et ecritures''. Brussells: Jean Leonard, 1691. | * LOAN courtesy of the Library of Congress. Claude Comiers. ''Traité de la parole, langues, et ecritures''. Brussells: Jean Leonard, 1691. LOC Call number: [http://lccn.loc.gov/96133051 Z103.5 .C67 1691 Fabyan Coll]. | ||
== How To Make Anything Signify Anything (zone 2)== | |||
[[File:Z103.T7 P6 F7 1625 Cage 2S4v.jpg|thumb|right|240px|''Polygraphie et universelle escriture caballistique'', 1625. Folger Digital Image [http://luna.folger.edu/luna/servlet/s/28od8a 94696].]] | |||
:''...the highest degree of cipher...is to signify anything by means of anything.... For by this art a way is opened, whereby a man may express and signify the intention of his mind, at any distance of place.... '' | :''...the highest degree of cipher...is to signify anything by means of anything.... For by this art a way is opened, whereby a man may express and signify the intention of his mind, at any distance of place.... '' | ||
::—Sir Francis Bacon on ciphers (1623) | ::—Sir Francis Bacon on ciphers (1623) | ||
| Line 83: | Line 95: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* Giovanni Battista Palatino. ''Compendio del gran volume de l’arte del bene et leggiadramente scrivere tutte le sorti di lettere et caratteri''. Rome: Heirs of Valerio and Luigi Dorici, 1566. Call number: Z43.A3 P3 1566 Cage; displayed | * Giovanni Battista Palatino. ''Compendio del gran volume de l’arte del bene et leggiadramente scrivere tutte le sorti di lettere et caratteri''. Rome: Heirs of Valerio and Luigi Dorici, 1566. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=108921 Z43.A3 P3 1566 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/6l2qjh F3v–F4r]. | ||
* Blaise de Vigenère. ''Traicté des chiffres, ou, Secretes manieres d’escrire''. Paris: Abel L’Angelier, 1586. Call number: Z103 .V6 1586 Cage; displayed | * Blaise de Vigenère. ''Traicté des chiffres, ou, Secretes manieres d’escrire''. Paris: Abel L’Angelier, 1586. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=263026 Z103 .V6 1586 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/59erm0 fol. 302v–303r ]. | ||
* Giambattista della Porta. ''De furtivis literarum notis''. London: John Wolfe, 1591. Call number: STC 20118 Copy 1; displayed p. 90–91 | * Giambattista della Porta. ''De furtivis literarum notis''. London: John Wolfe, 1591. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=158738 STC 20118 Copy 1]; displayed [http://luna.folger.edu/luna/servlet/s/4xb158 p. 90–91] and [http://luna.folger.edu/luna/servlet/s/d6p9ur LUNA Digital Image]. | ||
=== Stenography (case 7) === | === Stenography (case 7) === | ||
| Line 93: | Line 105: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* John Willis. ''The art of stenographie, teaching...the way of compendious writing''. London: W. White for Cuthbert Burbie, 1602. Call number: STC 25744a; displayed | * John Willis. ''The art of stenographie, teaching...the way of compendious writing''. London: W. White for Cuthbert Burbie, 1602. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=160648 STC 25744a]; displayed [http://luna.folger.edu/luna/servlet/s/lu59cc sig. A8v–B1r ]) and [http://luna.folger.edu/luna/servlet/s/45bfc5 title page] in facsimile. | ||
* Francis Bacon. ''De sapientia veterum''. London: Felix Kingston, 1634. Call number: STC 1129; displayed A3r additional title page | * Francis Bacon. ''De sapientia veterum''. London: Felix Kingston, 1634. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=158284 STC 1129]; displayed [http://luna.folger.edu/luna/servlet/s/p7b3vw A3r additional title page] and [http://luna.folger.edu/luna/servlet/s/224eyn LUNA Digital Image]. | ||
* Henry Oxinden | * Henry Oxinden. [[Miscellany of Henry Oxinden, ca. 1642-1670 V.b.110|Manuscript miscellany]], ca. 1642–70. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=226678 V.b.110]; displayed [http://luna.folger.edu/luna/servlet/s/1ey8e4 2nd leaf, verso] and [http://collation.folger.edu/2012/05/fruit-orchard/ Blog post, The Collation] and [http://luna.folger.edu/luna/servlet/s/814y6z LUNA Digital Copy]. | ||
* Thomas Shelton. ''Tachygraphy''. London: Samuel Simmons, 1674. Call number: | * Thomas Shelton. ''Tachygraphy''. London: Samuel Simmons, 1674. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=196268 262- 551q]; displayed [http://luna.folger.edu/luna/servlet/s/8jna4z p. 1] and [http://collation.folger.edu/2012/05/thomas-sheltons-shorthand-version-of-the-lords-prayer/ Blog post, The Collation] and [http://luna.folger.edu/luna/servlet/s/3l0o01 LUNA Digital Image]. | ||
=== Tables (case 8) === | === Tables (case 8) === | ||
| Line 104: | Line 116: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* LOAN courtesy of the Library of Congress. Johannes Trithemius. ''Polygraphiae libri sex''. [Basel]: Johann Haselberg, 1518. | * LOAN courtesy of the Library of Congress. Johannes Trithemius. ''Polygraphiae libri sex''. [Basel]: Johann Haselberg, 1518. LOC Call number [http://lccn.loc.gov/32017914 Z103 .T83 1518 Fabyan Coll] and [http://hdl.loc.gov/loc.rbc/fabyan.17914.1 LOC Digital Copy]. | ||
* LOAN courtesy of the Library of Congress. Giovan Battista Bellaso. ''La cifra''. Venice: 1553. | * LOAN courtesy of the Library of Congress. Giovan Battista Bellaso. ''La cifra''. Venice: 1553. LOC Call number: [http://lccn.loc.gov/77506528 Z103.5 .B44 Fabyan Coll]. | ||
* Blaise de Vigenère. ''Traicté des chiffres, ou, Secretes manieres d’escrire''. Paris: Abel L’Angelier, 1587. Call number: Z103 .V6 1587 Cage; displayed item 2 btwn. p. 184–185 | * Blaise de Vigenère. ''Traicté des chiffres, ou, Secretes manieres d’escrire''. Paris: Abel L’Angelier, 1587. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=263028 Z103 .V6 1587 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/8c96n9 item 2 btwn. p. 184–185] and [http://luna.folger.edu/luna/servlet/s/a80a1o LUNA Digital Image]. | ||
=== Bacon's Biliteral Cipher (case 9) === | === Bacon's Biliteral Cipher (case 9) === | ||
[[File:STC 1167 copy 1 2L1v.jpg|thumb|right|260px|Bacon's biliteral cipher. Folger Digital Image [http://luna.folger.edu/luna/servlet/s/p7thyv 94046].]] | |||
In the course of the sixteenth century, cryptographers found ways to reduce the entire alphabet to only a few letters—and the great scientist and statesman Sir Francis Bacon devised a system using just two. In Bacon's "biliteral" (or two-letter) system, each letter of the English alphabet is represented by a different five-letter combination of A's and B's, from AAAAA for A to BABBB for Z. What made Bacon's invention so powerful is that these A's and B's could be represented by two types of anything—roman and italic type, pluses and minuses, apples and oranges, and so on. Using this system, as Friedman was fond of quoting, "it is possible to signify ''omnia per omnia'' (anything by means of anything)." | |||
==== Friedman and the Biliteral Cipher ==== | |||
Friedman kept copies of a particular photo under the glass on his office desk and on the wall of his home study. It served as the graduation photo for his first course in military cryptanalysis, taught to a group of World War I officers sent to Riverbank for training. It remained his most cherished example of how to make anything signify anything using Bacon’s biliteral cipher. In this case, the A-types look at the camera and the B-types look away, using Bacon’s method of encryption to spell out his famous axiom, KNOWLEDGE IS POWER—which Friedman took as his personal motto and had inscribed on his tomb in Arlington National Cemetery. | |||
Watch a [http://www.youtube.com/watch?v=4C9phKLx2vU video] of curator, Dr. Bill Sherman, discussing the "Knowledge is Power" photograph. | |||
==== Items Included ==== | ==== Items Included ==== | ||
* Francis Bacon. ''Of the...advancement of learning''. London: Thomas Purfoot and Thomas Creede for Henrie Tomes, 1605. Call number: STC 1164 copy 1; displayed sig. 2Q1r | * Francis Bacon. ''Of the...advancement of learning''. London: Thomas Purfoot and Thomas Creede for Henrie Tomes, 1605. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=158409 STC 1164 copy 1]; displayed [http://luna.folger.edu/luna/servlet/s/2b9rg8 sig. 2Q1r]. | ||
* Francis Bacon. ''De dignitate & augmentis scientiarum''. London: John Haviland, 1623. Call number: STC 1108; displayed p. 278–279 | * Francis Bacon. ''De dignitate & augmentis scientiarum''. London: John Haviland, 1623. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=168533 STC 1108]; displayed [http://luna.folger.edu/luna/servlet/s/8ftx27 p. 278–279]. | ||
* Francis Bacon. ''Of the advancement and proficiencie of learning''. Oxford: Leonard Lichfield for Robert Young and Edward Forrest, 1640. Call number: STC 1167 copy 1; displayed p. 266 | * Francis Bacon. ''Of the advancement and proficiencie of learning''. Oxford: Leonard Lichfield for Robert Young and Edward Forrest, 1640. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=161760 STC 1167 copy 1]; displayed [http://luna.folger.edu/luna/servlet/s/5m4orw p. 266] and [http://luna.folger.edu/luna/servlet/s/85w35a LUNA Digital Image]. | ||
* LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. William F. Friedman. “KNOWLEDGE IS POWER.” Aurora, Ill., ca. January 1918. | * LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. William F. Friedman. “KNOWLEDGE IS POWER.” Aurora, Ill., ca. January 1918. | ||
| Line 122: | Line 140: | ||
The cipher disc may be the most iconic image in the history of cryptography. And for good reason: it puts a simple but powerful system of alphanumeric substitution into the palm of one's hand. In portable form, it was particularly well-suited for use in the field. Within the covers of the period's books, it became one of the primary applications of the new technology called the volvelle, where one circle (often featuring a pointing hand) could be turned on top of another, with each turn of the disk presenting a new cipher alphabet. | The cipher disc may be the most iconic image in the history of cryptography. And for good reason: it puts a simple but powerful system of alphanumeric substitution into the palm of one's hand. In portable form, it was particularly well-suited for use in the field. Within the covers of the period's books, it became one of the primary applications of the new technology called the volvelle, where one circle (often featuring a pointing hand) could be turned on top of another, with each turn of the disk presenting a new cipher alphabet. | ||
Friedman's friend, the classicist and cryptanalyst Charles J. Mendelsohn, considered Giambattista della Porta the outstanding cryptographer of the Renaissance. He had a particularly solid grasp of the use of cipher disks, explaining how they can be converted into tables and vice versa. His books featured some of the period's most ornate volvelles. | |||
==== Items Included ==== | ==== Items Included ==== | ||
| Line 127: | Line 147: | ||
===== Case 10 ===== | ===== Case 10 ===== | ||
* Jacopo Silvestri. ''Opus novum''. Rome: Marcello Silber, 1526. Call number: Z103 .S5 1526 Cage; displayed | * Jacopo Silvestri. ''Opus novum''. Rome: Marcello Silber, 1526. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=263022 Z103 .S5 1526 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/m7454v fol. 6v]. | ||
* Giambattista della Porta. ''De furtivis literarum notis''. London: John Wolfe, 1591. Call number: STC 20118a; displayed p. 72–73 | * Giambattista della Porta. ''De furtivis literarum notis''. London: John Wolfe, 1591. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=165675 STC 20118a]; displayed [http://luna.folger.edu/luna/servlet/s/gf2o60 p. 72–73] and [http://luna.folger.edu/luna/servlet/s/tcfky4 LUNA Digital Image]. | ||
* Johannes Trithemius | * Johannes Trithemius. ''Polygraphie et universelle escriture caballistique''. Paris: Jacques Kerver, 1625. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=338165 Z103.T7 P6 F7 1625 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/3gaf2k p. 328]. | ||
===== Wall Panel ===== | ===== Wall Panel ===== | ||
* Leon Battista Alberti. ''Opuscoli morali''. Venice: Francesco di Franceschi, 1568. Call number: PQ4562 .A6 1568 Cage. | * Leon Battista Alberti. ''Opuscoli morali''. Venice: Francesco di Franceschi, 1568. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=110610 PQ4562 .A6 1568 Cage] and [http://luna.folger.edu/luna/servlet/s/blnjba LUNA Digital Image]. | ||
=== Grilles (case 11) === | === Grilles (case 11) === | ||
The popular scientist Girolamo Cardano was credited with an invention that is still in use today. In the so-called "Cardan grille" a sheet with irregular holes cut in it is laid over a blank page and the intended message is written in the spaces. The sheet is then removed and the rest of the spaces are filled in with innocent—or even misleading—text. When the recipient lays the same grid over the letter in the same position, the hidden message is revealed. | The popular scientist Girolamo Cardano was credited with an invention that is still in use today. In the so-called "Cardan grille" a sheet with irregular holes cut in it is laid over a blank page and the intended message is written in the spaces. The sheet is then removed and the rest of the spaces are filled in with innocent—or even misleading—text. When the recipient lays the same grid over the letter in the same position, the hidden message is revealed. | ||
Della Porta’s popular treatise on secret writing includes clear instructions for using a grille—or a membrane, as he describes it—with windows and gaps (''fenestras et vacua''). To make sure that the recipient knows where to place the overlay, four points should be drawn to mark the edges. | |||
==== Items Included ==== | ==== Items Included ==== | ||
* Girolamo Cardano. ''De rerum | * Girolamo Cardano. ''Hieronymi Cardani Mediolanensis medici De rerum uarietate libri XVII''. Basel: Heinrich Petri, 1557. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=89811 156- 884f]; displayed [http://luna.folger.edu/luna/servlet/s/oy63te title page]. | ||
* Giambattista della Porta. De occultis literarum notis. Montbéliard: Jacques Foillet and Lazarus Zetzner, 1593. Call number: 173- 568.1q; displayed | * Giambattista della Porta. ''De occultis literarum notis seu Artis animi sensa occulte alijs significandi''. Montbéliard: Jacques Foillet and Lazarus Zetzner, 1593. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=221140 173- 568.1q]; displayed [http://luna.folger.edu/luna/servlet/s/o727x8 p. 134]. | ||
* LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. William F. Friedman and Elizebeth S. Friedman. Cryptographic Christmas Card for 1928. | * LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. William F. Friedman and Elizebeth S. Friedman. [http://marshallfoundation.org/blog/friedmans-christmas-cards/ Cryptographic Christmas Card for 1928]. | ||
* LOAN courtesy of the Massachusetts Historical Society. John Clotworthy, viscount Masereene. Autograph letter to John Winthrop, Jr., with grille. Dublin, 6 March 1634/35. | * LOAN courtesy of the [http://www.masshist.org Massachusetts Historical Society]. John Clotworthy, viscount Masereene. Autograph letter to John Winthrop, Jr., with grille. Dublin, 6 March 1634/35. [http://www.masshist.org/collection-guides/view/fa0294 Collection guide to the Winthrop Family Papers, 1537–1990]. | ||
=== Say It with Flowers (case 12) === | === Say It with Flowers (case 12) === | ||
| Line 152: | Line 174: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* FACSIMILE from the Bacon cipher collection | * FACSIMILE from the Bacon cipher collection. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox and Tilden Foundations. Cora Jensen [and William F. Friedman]. "‘Saying It’ in Cipher." ''Florists’ Review'', 1920. NYPL Call number: [http://archives.nypl.org/mss/176#overview MssCol 176]. | ||
* LOAN courtesy of the Library of Congress. Johann Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. | * LOAN courtesy of the Library of Congress. Johann Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. LOC Call number: [http://lccn.loc.gov/77502325 Z103.5 .F75 1685 Fabyan Coll]. | ||
* LOAN courtesy of the Library of Congress. Loose-leaf note from Friedman’s team at Riverbank in Johann Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. | * LOAN courtesy of the Library of Congress. Loose-leaf note from Friedman’s team at Riverbank in Johann Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. LOC Call number: [http://lccn.loc.gov/77502325 Z103.5 .F75 1685 Fabyan Coll]. | ||
* FACSIMILE from the Bacon cipher collection | * FACSIMILE from the Bacon cipher collection. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox and Tilden Foundations. [Cora Jensen and William F. Friedman]. “‘Saying It’ in Cipher.” Typescript, 1920. NYPL Call number: [http://archives.nypl.org/mss/176#overview MssCol 176]. | ||
=== Music (case 13)=== | === Music (case 13)=== | ||
Music was another signifying system that could be used both to convey and to cover secret messages, with particular notes standing in for the different letters in the alphabet. The systems shown in this case made it possible for musical compositions to speak to people even when they did not contain words. | Music was another signifying system that could be used both to convey and to cover secret messages, with particular notes standing in for the different letters in the alphabet. The systems shown in this case made it possible for musical compositions to speak to people even when they did not contain words. | ||
As in other examples, Friedman used the sheet music (arranged for solo mandolin) for Stephen Foster's famous song, "My Old Kentucky Home, Good Night" to show how, using Bacon's biliteral cipher, anything can be made to signify anything. By making notches in the stems of some notes and leaving others whole, he has turned the music into a sequence of a's and b's that read "Enemy advancing right / We march at daybreak." | |||
==== Items Included ==== | ==== Items Included ==== | ||
* FACSIMILE (adapted with message deciphered) from the Bacon cipher collection | * FACSIMILE (adapted with message deciphered) from the Bacon cipher collection. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox and Tilden Foundations. William F. Friedman. "My Old Kentucky Home, Good Night". Modified sheet music, 1916. NYPL Call number: [http://archives.nypl.org/mss/176#overview MssCol 176]. | ||
* John Wilkins. ''Mercury: or, The secret and swift messenger''. London: | * John Wilkins. ''Mercury: or, The secret and swift messenger''. London: for Richard Baldwin, 1694. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=156450 W2203]; displayed [http://luna.folger.edu/luna/servlet/s/wuoj6u p. 144–45 ]. | ||
* LOAN courtesy of the Library of Congress. Johannes Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. | * LOAN courtesy of the Library of Congress. Johannes Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. LOC Call number: [http://lccn.loc.gov/77502325 Z103.5 .F75 1685 Fabyan Coll]. | ||
* Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. ''Cryptomenytices et cryptographiae libri IX''. Lüneburg: Johann and Heinrich Stem, 1623. Call number: Z103 .A9 1624 Cage; displayed | * Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. ''Cryptomenytices et cryptographiae libri IX''. Lüneburg: Johann and Heinrich Stem, 1623. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=263027 Z103 .A9 1624 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/08fq27 p. 324–35]. | ||
=== Steganography (case 14) === | === Steganography (case 14) === | ||
| Line 174: | Line 198: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* Johannes Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. Call number: 166- 900q; displayed | * Johannes Balthasar Friderici. ''Cryptographia''. Hamburg: Georg Rebenlein, 1685. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=335507 166- 900q]; displayed [http://luna.folger.edu/luna/servlet/s/9967yn loose leaf opp. p. 217]. | ||
* LOAN courtesy of the Library of Congress. Blaise de Vigenère. ''Traicté des chiffres, ou, Secretes manieres d’escrire''. Paris: Abel L’Angelier, 1587. | * LOAN courtesy of the Library of Congress. Blaise de Vigenère. ''Traicté des chiffres, ou, Secretes manieres d’escrire''. Paris: Abel L’Angelier, 1587. LOC Call number: [http://lccn.loc.gov/96153330 Z103.5 .V54 1587 Fabyan Coll] | ||
* Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. ''Cryptomenytices et cryptographiae libri IX''. Lüneburg: Johann and Heinrich Stem, 1624. Call number: Z103 .A9 1623 Cage; displayed | * Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. ''Cryptomenytices et cryptographiae libri IX''. Lüneburg: Johann and Heinrich Stem, 1624. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=263037 Z103 .A9 1623 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/72kolf p. 340–41]. | ||
== Enigmas and Machines (zone 3) == | |||
[[File:170- 941q opp. M2r.jpg|thumb|right|320px|''Schola steganographica'', 1680. Folger Digital Image [http://luna.folger.edu/luna/servlet/s/76un2o 83922].]] | |||
:''Bacon was, in fact, the inventor of the binary code that forms the basis of modern electronic digital computers.'' | :''Bacon was, in fact, the inventor of the binary code that forms the basis of modern electronic digital computers.'' | ||
::—William F. Friedman, Six Lectures on Cryptology (1959–61) | ::—William F. Friedman, Six Lectures on Cryptology (1959–61) | ||
| Line 186: | Line 210: | ||
Well before the advent of digital technology, those working in the field of cryptography turned to machines to make the production and transmission of secret messages easier, faster, and more secure. Many of these devices (from Alberti's introduction of the cipher disk in the 1460s to the rotor-based SIGABA machine invented by Friedman and his colleagues in the 1930s) used single or multiple wheels to systematize the scrambling of letters. Friedman lived just long enough to see his field transformed by the introduction of computers—and to claim that "Bacon was the inventor of the binary code" on which they depend. | Well before the advent of digital technology, those working in the field of cryptography turned to machines to make the production and transmission of secret messages easier, faster, and more secure. Many of these devices (from Alberti's introduction of the cipher disk in the 1460s to the rotor-based SIGABA machine invented by Friedman and his colleagues in the 1930s) used single or multiple wheels to systematize the scrambling of letters. Friedman lived just long enough to see his field transformed by the introduction of computers—and to claim that "Bacon was the inventor of the binary code" on which they depend. | ||
==== SIGABA Machine ==== | |||
In the 1930s, William Friedman and Frank Rowlett (Army) and Commander Laurance Safford (Navy) invented an improved cipher machine for use by both forces: it was known as SIGABA in the Army and ECM (for Electric Code Machine) Mark II in the Navy. The basic operation was similar to the Enigma machine used by the Germans, but the Americans increased the number of rotors and improved the randomization of their movement. Unlike the Enigma, the SIGABA was never broken: it remained in use through the 1950s and was not declassified until 2000. | |||
==== Cyclologic Cryptographic Machine ==== | |||
In 1666, Samuel Mordland published ''A new method of cryptography'', considered today one of the rarest books in the field. This short treatise on cryptography drew on his work intercepting and decoding coded correspondence during the English Civil War (1642–51). It culminates in a “Cyclologic Cryptographic Machine,” illustrated on the book’s final page: using a series of cipher-wheels turned by a stylus, it was closely related to the mechanical adding machine he invented the same year. | |||
==== Items Included ==== | ==== Items Included ==== | ||
* LOAN courtesy of the National Cryptologic Museum, NSA. William F. Friedman. SIGABA machine. | * LOAN courtesy of the [https://www.nsa.gov/about/cryptologic_heritage/museum/virtual_tour/museum_tour_text.shtml#big_machines National Cryptologic Museum], NSA. William F. Friedman. SIGABA machine. | ||
* FACSIMILE from the National Cryptologic Museum, NSA. US patent 6,175,625. January 16, 2001. | * FACSIMILE from the National Cryptologic Museum, NSA. US patent 6,175,625. January 16, 2001. [http://pdfpiw.uspto.gov/.piw?PageNum=0&docid=06175625&IDKey=0FDA2604F60C&HomeUrl=http%3A%2F%2Fpatft.uspto.gov%2Fnetacgi%2Fnph-Parser%3FSect1%3DPTO1%2526Sect2%3DHITOFF%2526d%3DPALL%2526p%3D1%2526u%3D%25252Fnetahtml%25252FPTO%25252Fsrchnum.htm%2526r%3D1%2526f%3DG%2526l%3D50%2526s1%3D6175625.PN.%2526OS%3DPN%2F6175625%2526RS%3DPN%2F6175625 Digital Copy of Patent] | ||
* Samuel Morland. ''A new method of cryptography''. London: 1666. Call number: M2781A; displayed p. 12 | * Samuel Morland. ''A new method of cryptography''. London: 1666. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=147537 M2781A]; displayed [http://luna.folger.edu/luna/servlet/s/h3s6o9 p. 12] and [http://luna.folger.edu/luna/servlet/s/5b0hf3 LUNA Digital Image]. | ||
* LOAN courtesy of the Preservation Partners of the Fox Valley and Kane County Forest Preserve District. Wheatstone-Plett Cipher Device. From George Fabyan’s collection at Riverbank Laboratories. | * LOAN courtesy of the [https://ppfv.org/fabyan-villa/ Preservation Partners of the Fox Valley and Kane County Forest Preserve District]. Wheatstone-Plett Cipher Device. From George Fabyan’s collection at Riverbank Laboratories. | ||
=== Kircher's Cryptographic Machines (case 16) === | === Kircher's Cryptographic Machines (case 16) === | ||
| Line 200: | Line 231: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* Gaspar Schott. ''Schola steganographica''. Nuremberg: Heirs of Johann and Wolfgang Endter, 1680. Call number: 170- 941q; displayed | * Gaspar Schott. ''Schola steganographica''. Nuremberg: Heirs of Johann and Wolfgang Endter, 1680. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=335511 170- 941q]; displayed [http://luna.folger.edu/luna/servlet/s/qzv4bv opp. p. 91]. | ||
* Athanasius Kircher. ''Magnes sive De arte magnetic''. Rome: Biaggio Diversin, Zenobio Masotti, and Vitale Mascardi, 1654. Call number: 166- 834f; displayed | * Athanasius Kircher. ''Magnes sive De arte magnetic''. Rome: Biaggio Diversin, Zenobio Masotti, and Vitale Mascardi, 1654. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=335514 166- 834f]; displayed [http://luna.folger.edu/luna/servlet/s/4373km p. 290–91]. | ||
=== The Voynich Mystery (case 17) === | === The Voynich Mystery (case 17) === | ||
In 1912, a rare book dealer named Wilfrid M. Voynich acquired a cache of manuscripts from a Jesuit college near Rome. Among them was the strange codex that now bears his name, a heavily illustrated text on vellum, carefully written by an unknown author in an elaborate script or symbol system that has never been deciphered. The great Chaucerian (and World War I code-breaker) John M. Manly, one of the first scholars to examine the volume, described it as "the most mysterious manuscript in the world," and a full century after it resurfaced we still know surprisingly little about it. The cracking of the Voynich Code—if that is what it is—has long been a holy grail for students of cryptography. Research from other angles (including the history of botanical illustration and the use of computers to analyze patterns) continues to generate fresh theories that keep the manuscript in the news. We hope that this exhibition will provide new information and inspiration for the amateur and professional scholars who fall under its spell. | In 1912, a rare book dealer named Wilfrid M. Voynich acquired a cache of manuscripts from a Jesuit college near Rome. Among them was the strange codex that now bears his name, a heavily illustrated text on vellum, carefully written by an unknown author in an elaborate script or symbol system that has never been deciphered. The great Chaucerian (and World War I code-breaker) John M. Manly, one of the first scholars to examine the volume, described it as "the most mysterious manuscript in the world," and a full century after it resurfaced we still know surprisingly little about it. The cracking of the Voynich Code—if that is what it is—has long been a holy grail for students of cryptography. Research from other angles (including the history of botanical illustration and the use of computers to analyze patterns) continues to generate fresh theories that keep the manuscript in the news. We hope that this exhibition will provide new information and inspiration for the amateur and professional scholars who fall under its spell. | ||
Historian [http://www.voynich.nu/index.html René Zandbergen's website] provides more detailed information on this curious manuscript. | |||
==== Items Included ==== | ==== Items Included ==== | ||
* LOAN courtesy of the Beinecke Library, Yale University. ''The Voynich Manuscript''. (ca. 1410–30). | * LOAN courtesy of the Beinecke Library, Yale University. ''The Voynich Manuscript''. (ca. 1410–30). Yale Call number: [http://hdl.handle.net/10079/bibid/11167038 Beinecke MS 408] and [http://brbl-dl.library.yale.edu/vufind/Record/3519597 Beinecke Digital Manuscript]. | ||
=== The Friedmans and the Folger (case 18) === | === The Friedmans and the Folger (case 18) === | ||
| Line 217: | Line 250: | ||
==== Items Included ==== | ==== Items Included ==== | ||
* William F. Friedman and Elizebeth S. Friedman. ''The cryptologist looks at Shakespeare''. Typescript, 1954. Call number: Y.d.76; displayed chapters 1–6 stacked, | * William F. Friedman and Elizebeth S. Friedman. ''The cryptologist looks at Shakespeare''. Manuscript. Typescript, 1954. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=217559 Y.d.76]; displayed chapters 1–6 stacked, [http://luna.folger.edu/luna/servlet/s/9ql0gn title page] on top. | ||
* William F. Friedman and Elizebeth S. Friedman. ''The Shakespearean Ciphers Examined''. Cambridge: Cambridge University Press, 1957. Call number: PR2937 .F7 1957 Copy 2 Cage; displayed | * William F. Friedman and Elizebeth S. Friedman. ''The Shakespearean Ciphers Examined''. Cambridge: Cambridge University Press, 1957. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=52477 PR2937 .F7 1957 Copy 2 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/g7z3yz front endleaf 1r]. | ||
* LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Washington Post, April 3, 1955 | * LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Washington Post, April 3, 1955 | ||
| Line 224: | Line 257: | ||
After the Bacon-Shakespeare controversy, the Friedmans' favorite extracurricular project was the Voynich Manuscript. As his country's leading expert on secret writing systems, William Friedman was quickly enlisted to solve the Voynich mystery. During three different periods of sustained study (in the 1920s, 40s, and 60s), Friedman threw all available resources at the problem, including some of the earliest use of computer-assisted text analysis. But the manuscript stubbornly refused to yield its secrets to Friedman (as it had to Kircher when he was consulted in 1666), and he died with only vague theories and not a single line of deciphered text. | After the Bacon-Shakespeare controversy, the Friedmans' favorite extracurricular project was the Voynich Manuscript. As his country's leading expert on secret writing systems, William Friedman was quickly enlisted to solve the Voynich mystery. During three different periods of sustained study (in the 1920s, 40s, and 60s), Friedman threw all available resources at the problem, including some of the earliest use of computer-assisted text analysis. But the manuscript stubbornly refused to yield its secrets to Friedman (as it had to Kircher when he was consulted in 1666), and he died with only vague theories and not a single line of deciphered text. | ||
==== Friedman on the Voynich Solution ==== | |||
In a typical display of cryptic wit, Friedman recorded his final theory about the Voynich Manuscript in the form of an anagram, and embedded it into the final paragraph of his 1959 article on anagrams in Chaucer—rearranging the letters by hand and filing the cut-out tiles in his archive. The solution was kept in a sealed envelope and only published after his death: | |||
:''“The Voynich MS was an early attempt to construct an artificial or universal language of the a priori type. —Friedman.”'' | |||
Friedman felt, in the end, that there was no code to be broken but rather an entirely invented language whose rules we do not yet know. | |||
==== Items Included ==== | ==== Items Included ==== | ||
* LOAN courtesy of the George C. Marshall Foundation. William F. Friedman and the Voynich Manuscript Study Group. Voynich character frequency tables, ca. 1944. | * LOAN courtesy of the George C. Marshall Foundation. William F. Friedman and the Voynich Manuscript Study Group. Voynich character frequency tables, ca. 1944. [http://marshallfoundation.org/library/collection/william-f-friedman-papers/#!/collection=85 Collection of William F. Friedman Papers]. | ||
* LOAN courtesy of the George C. Marshall Foundation. William F. Friedman and the Voynich Manuscript Study Group. Agreed alphabet for transcription of Voynich characters. June 13, 1944 | * LOAN courtesy of the George C. Marshall Foundation. William F. Friedman and the Voynich Manuscript Study Group. Agreed alphabet for transcription of Voynich characters. June 13, 1944 | ||
* LOAN courtesy of the George C. Marshall Foundation. Lexington, VA. RCA Computer run of characters from the Voynich Manuscript, ca. 1962 | * LOAN courtesy of the George C. Marshall Foundation. Lexington, VA. RCA Computer run of characters from the Voynich Manuscript, ca. 1962 | ||
=== Puzzling Pages (case 20) === | === Puzzling Pages (case 20) === | ||
[[File:Y.d.1009(2b) puzzle.jpg|thumb|right|250px|Shakespearean puzzle solved by the Folgers. Folger Digital Image [http://luna.folger.edu/luna/servlet/s/6adaa9 83910].]] | |||
People who have the qualities of mind needed to make and break codes often delight in puzzles. There has long been a close affinity between cryptanalysts and crossword puzzles, and Friedman was one of many who got their first introduction to the field through Edgar Allan Poe—who wrote a regular newspaper column in which he solved ciphers sent in to him by readers and whose famous story "The Gold Bug" played a major role in popularizing cryptograms. | People who have the qualities of mind needed to make and break codes often delight in puzzles. There has long been a close affinity between cryptanalysts and crossword puzzles, and Friedman was one of many who got their first introduction to the field through Edgar Allan Poe—who wrote a regular newspaper column in which he solved ciphers sent in to him by readers and whose famous story "The Gold Bug" played a major role in popularizing cryptograms. | ||
==== Items Included ==== | ==== Items Included ==== | ||
* Athanasius Kircher. ''Polygraphia nova et universalis ex combinatoria arte detecta''. Rome: Lazzari Varese, 1663. Call number: Folio P361 .K5 1663 Cage; displayed p. 23 | * Athanasius Kircher. ''Polygraphia nova et universalis ex combinatoria arte detecta''. Rome: Lazzari Varese, 1663. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=335513 Folio P361 .K5 1663 Cage]; displayed [http://luna.folger.edu/luna/servlet/s/5h8m07 p. 23]. | ||
*Henry Clay Folger and Emily C. J. Folger. Solution to "Shakespearean Enigma" crossword. ''New York Herald Tribune'', March 15, 1925. Call number: Y.d.1009; displayed 2b | *Henry Clay Folger and Emily C. J. Folger. Solution to "Shakespearean Enigma" crossword. ''New York Herald Tribune'', March 15, 1925. Call number: [http://hamnet.folger.edu/cgi-bin/Pwebrecon.cgi?BBID=231114 Y.d.1009]; displayed [http://luna.folger.edu/luna/servlet/s/w250xs 2b] and [http://luna.folger.edu/luna/servlet/s/plf1b6 LUNA Digital Image]. | ||
* LOAN courtesy of the George C. Marshall Foundation, William F. Friedman and Elizebeth S. Friedman. Cryptographic dinner menu, May 15, 1929. | * LOAN courtesy of the George C. Marshall Foundation, William F. Friedman and Elizebeth S. Friedman. Cryptographic dinner menu, May 15, 1929. | ||
[[Category: Public programs]] | [[Category: Public programs]] | ||
[[Category: Exhibitions]] | [[Category: Exhibitions]] | ||
Latest revision as of 12:04, 15 July 2015
This article offers a comprehensive and descriptive list of each piece included in the Decoding the Renaissance: 500 Years of Codes and Ciphers, one of the Exhibitions at the Folger.
This exhibition was arranged into three zones: The Renaissance of Cryptography; How To Make Anything Signify Anything; and Enigmas and Machines.
The Renaissance of Cryptography (zone 1)

- ...a familiarity with the conditions and customs of [the sixteenth and seventeenth centuries] will bring one to the conclusion that there were, indeed, very few things in those days that did not have something to do with ciphers.
- —William F. Friedman, "Saying it in Cipher" (1920)
The Birth of the Cryptographic Book (case 1)
The Renaissance was the first great age of mass communication, but it was also the period when the art of secret writing came into its own. The new science of codes and ciphers produced some of the period’s most brilliant inventions, most beautiful books, and most enduring legacies.
One of the oldest cryptographic books was written by the quintessential Renaissance Man, Leon Battista Alberti. His short text on ciphers, Opuscoli morali, first published in this 1568 collection, was written a century earlier, making it Europe’s oldest extant treatise on ciphers and earning Alberti the title of Father of Western Cryptology.
However, the first printed cryptographic book was Trithemius’ posthumous work on polygraphic (or multiple writing) systems, Polygraphiae libri sex. The title-page depicts Trithemius presenting the book to its dedicatee, Emperor Maximilian I. The monk behind him provides the keys to the locked book, whose secrets are central to the exercise of power in church and state.
Items Included
- Leon Battista Alberti. Opuscoli morali. Venice: Francesco di Franceschi, 1568. Call number: PQ4562 .A6 1568 Cage; displayed sig. A1v and LUNA Digital Image.
- Johannes Trithemius. Polygraphiae libri sex. [Basel?]: Johann Haselberg, 1518. Call number: Folio Z103.T7 P6 1518 Cage; displayed title page.
The First Cryptographic Couple (case 2 and wall panel)
William Frederick Friedman (1891–1969) and Elizebeth Smith Friedman (1892–1980) are sometimes described as the nation's First Cryptographic Couple. They were introduced to the subject and to each other by the larger-than-life textile magnate George Fabyan at Riverbank, a country estate and research institute near Chicago. They joined a team providing support for Elizabeth Wells Gallup, the leading advocate of the popular idea that Francis Bacon had written Shakespeare's works and left ciphered clues throughout the 1623 First Folio and other texts. The Friedmans quickly lost faith in this theory and moved to Washington, where William ran the Signals Intelligence Service and Elizebeth worked for the Coast Guard and other agencies. But they continued their study of the Renaissance and eventually settled on Capitol Hill. Many of the books they used at Riverbank are now housed across the street in the Fabyan Collection at the Library of Congress.
The Friedmans and Shakespeare
After leaving Riverbank in 1920, the Friedmans remained in close contact with Elizabeth Wells Gallup and her fellow Baconians, collecting materials for this comprehensive critique of the Baconian authorship theory. By the late 1940s, they were giving lectures called “The Cryptologist Looks at Shakespeare.” Their original typescript (bearing that earlier title) was finished in 1954 and the revised book was published to great acclaim three years later by Cambridge University Press.
Items Included
Case 2
- LOAN courtesy of the Library of Congress. William F. Friedman. Methods for the Solutions of Ciphers. Geneva, Ill.: Riverbank Laboratories, 1917–22.
- LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Exceptional Civilian Service Medal. Presented to William F. Friedman in 1944.
- LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Medal for Merit. Presented to William F. Friedman in 1946.
- William F. Friedman and Elizebeth S. Friedman. The Shakespearean Ciphers Examined. Cambridge: Cambridge University Press, 1957. Call number: PR2937 .F7 1957 Copy 2 Cage and LUNA Digital Image.
- LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Photo of William F. Friedman and Elizebeth S. Friedman, ca. 1957. 310 2nd Street SE, Washington, DC.
Wall Panel
- LOAN courtesy of the Bacon cipher collection, 1893–1948. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox, and Tilden Foundations. William F. Friedman. Cipher Baconis Gallup. Manuscript, ca. March 1916. NYPL Call number: MssCol 176.
Invisible Ink (case 3)
Not all secret communication depends on codes and ciphers, and one of the oldest tricks in the book was to make the message itself invisible. Using nothing more than materials found in the average kitchen—lemon juice and a candle—it is possible to make written letters disappear and reappear at will.
Items Included
- John Wilkins.. Mercury; or the secret and swift messenger. London: J. Norton for John Maynard and Timothy Wilkins, 1641. Call number: W2202; displayed p. 42–43.
- Miscellaneous collection of recipes. Manuscript, ca. 1600. Call number: V.a.140; displayed fol. 14v.
- LOAN courtesy of the Library of Congress. H. O. Nolan. The Production and Detection of Messages in Concealed Writing and Images. Geneva, Ill.: Riverbank Laboratories, 1918. LOC Call number: Z104.5 .N65 1918b.
Secretaries, Scribes, and Ciphers (case 4 and wall panel)

The cryptographic book emerged with—and through—the invention of moveable type, but people had been using cryptographic means to secure their communications for centuries before the advent of print. Diplomatic and commercial business throughout the Medieval and Early Modern periods depended heavily on handwritten codes and ciphers: official correspondence and private documents alike are peppered with mysterious symbols designed to be read only by those who had the key to the system.
Sir Francis Walsingham
Widely known and feared as England's first spymaster, Secretary of State Sir Francis Walsingham used every trick in the book to search out secrets among his enemies while keeping his own communications secure. In the letter to the right of this text, he communicates Queen Elizabeth's wishes as the King of France was on his deathbed: he advises "great circumspection" in "the matter" and urges those involved to "beware whom they trust." He is careful to put the most sensitive information into cipher. You can see one of his ciphered letters on the right.
Sir Francis Bacon
In addition to leaving secret codes in Shakespeare's plays (a theory that has proven unfounded), famous politician Sir Francis Bacon is known for providing the first English summary of the science of ciphers in his famous work Of the Advancement of Learning. In this text, he describes his own invention—"while just a teenager"—of the so-called biliteral cipher. The original 1605 edition mentions the episode only in passing; but the extended Latin edition of 1623 and its English version of 1640 explain the system in detail and show how it works in practice.
Items Included
Case 4
- Sir Francis Walsingham. Autograph letter, partly in cipher, to unknown recipient, May 26, 1574. Manuscript compilation, 17th or 18th century. Call number: V.b.264, before p. 435; displayed item 5 btwn. p. 434–435.
- Leonhart Fuchs. De historia stirpium commentarij insignes maximis impensis et uigilijs elaborati. Basel: Michael Isingrin, 1542. Call number: 245- 323f; displayed back endleaf 3r and LUNA Digital Image.
Wall Panel
- George Digby. Autograph letter signed from George Digby, Oxford, to Prince Rupert or Prince Maurice. Coded letter written for King Charles I. 27 April 1645. Call number X.c.125; displayed p. 1 and LUNA Digital Image.
The Secret Science at a Glance (case 5)
A new field has been well and truly established when it can be divided into parts and displayed in a single view. By the end of the sixteenth century, books on cryptography could offer systematic surveys of enough techniques and technologies to fill sprawling diagrams that dazzled the eyes and boggled the mind.
Items Included
- LOAN courtesy of the Library of Congress. Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. Cryptomenytices et cryptographiae libri IX. Lüneburg: Johann and Heinrich Stem, 1624. LOC Call number: Z103 .A95.
- LOAN courtesy of the Library of Congress. Claude Comiers. Traité de la parole, langues, et ecritures. Brussells: Jean Leonard, 1691. LOC Call number: Z103.5 .C67 1691 Fabyan Coll.
How To Make Anything Signify Anything (zone 2)

- ...the highest degree of cipher...is to signify anything by means of anything.... For by this art a way is opened, whereby a man may express and signify the intention of his mind, at any distance of place....
- —Sir Francis Bacon on ciphers (1623)
Alphabets (case 6)
For Friedman, the pen was mightier than the sword: as he put it in his Six Lectures on Cryptology, "the greatest and the most powerful instrument or weapon ever forged or improved by man...is the weapon of literacy...and the most important invention, the one that made the weapon of literacy practical, was the invention of the alphabet." Letters themselves were cryptography's secret weapon and they had as much power to change the course of battles as bullets and bombs.
Items Included
- Giovanni Battista Palatino. Compendio del gran volume de l’arte del bene et leggiadramente scrivere tutte le sorti di lettere et caratteri. Rome: Heirs of Valerio and Luigi Dorici, 1566. Call number: Z43.A3 P3 1566 Cage; displayed F3v–F4r.
- Blaise de Vigenère. Traicté des chiffres, ou, Secretes manieres d’escrire. Paris: Abel L’Angelier, 1586. Call number: Z103 .V6 1586 Cage; displayed fol. 302v–303r .
- Giambattista della Porta. De furtivis literarum notis. London: John Wolfe, 1591. Call number: STC 20118 Copy 1; displayed p. 90–91 and LUNA Digital Image.
Stenography (case 7)
By the end of the sixteenth century, abbreviated alphabetical systems had emerged to improve the speed and secrecy of writing. "Shorthand" became widely available through popular manuals, and Samuel Pepys used it to protect his famous diary from prying eyes. Like cryptographic systems, shorthand methods replaced letters, syllables, and whole words with arbitrary symbols. This made them available, in fact, as codes and ciphers, and many authors in the field pointed to the close relationship between stenography (speedy writing) and steganography (hidden writing).
Items Included
- John Willis. The art of stenographie, teaching...the way of compendious writing. London: W. White for Cuthbert Burbie, 1602. Call number: STC 25744a; displayed sig. A8v–B1r ) and title page in facsimile.
- Francis Bacon. De sapientia veterum. London: Felix Kingston, 1634. Call number: STC 1129; displayed A3r additional title page and LUNA Digital Image.
- Henry Oxinden. Manuscript miscellany, ca. 1642–70. Call number: V.b.110; displayed 2nd leaf, verso and Blog post, The Collation and LUNA Digital Copy.
- Thomas Shelton. Tachygraphy. London: Samuel Simmons, 1674. Call number: 262- 551q; displayed p. 1 and Blog post, The Collation and LUNA Digital Image.
Tables (case 8)
Alphanumeric tables are one of the first great technical inventions in the field of cryptography, and it may not be an accident that they emerged with the advent of moveable type. They took advantage of what the printing press did especially well—distributing permutations of individual letters and numbers in a square or rectangular grid—and they made the work of substituting plain-text with cipher-text easier, more accurate, and far more secure.
Items Included
- LOAN courtesy of the Library of Congress. Johannes Trithemius. Polygraphiae libri sex. [Basel]: Johann Haselberg, 1518. LOC Call number Z103 .T83 1518 Fabyan Coll and LOC Digital Copy.
- LOAN courtesy of the Library of Congress. Giovan Battista Bellaso. La cifra. Venice: 1553. LOC Call number: Z103.5 .B44 Fabyan Coll.
- Blaise de Vigenère. Traicté des chiffres, ou, Secretes manieres d’escrire. Paris: Abel L’Angelier, 1587. Call number: Z103 .V6 1587 Cage; displayed item 2 btwn. p. 184–185 and LUNA Digital Image.
Bacon's Biliteral Cipher (case 9)

In the course of the sixteenth century, cryptographers found ways to reduce the entire alphabet to only a few letters—and the great scientist and statesman Sir Francis Bacon devised a system using just two. In Bacon's "biliteral" (or two-letter) system, each letter of the English alphabet is represented by a different five-letter combination of A's and B's, from AAAAA for A to BABBB for Z. What made Bacon's invention so powerful is that these A's and B's could be represented by two types of anything—roman and italic type, pluses and minuses, apples and oranges, and so on. Using this system, as Friedman was fond of quoting, "it is possible to signify omnia per omnia (anything by means of anything)."
Friedman and the Biliteral Cipher
Friedman kept copies of a particular photo under the glass on his office desk and on the wall of his home study. It served as the graduation photo for his first course in military cryptanalysis, taught to a group of World War I officers sent to Riverbank for training. It remained his most cherished example of how to make anything signify anything using Bacon’s biliteral cipher. In this case, the A-types look at the camera and the B-types look away, using Bacon’s method of encryption to spell out his famous axiom, KNOWLEDGE IS POWER—which Friedman took as his personal motto and had inscribed on his tomb in Arlington National Cemetery.
Watch a video of curator, Dr. Bill Sherman, discussing the "Knowledge is Power" photograph.
Items Included
- Francis Bacon. Of the...advancement of learning. London: Thomas Purfoot and Thomas Creede for Henrie Tomes, 1605. Call number: STC 1164 copy 1; displayed sig. 2Q1r.
- Francis Bacon. De dignitate & augmentis scientiarum. London: John Haviland, 1623. Call number: STC 1108; displayed p. 278–279.
- Francis Bacon. Of the advancement and proficiencie of learning. Oxford: Leonard Lichfield for Robert Young and Edward Forrest, 1640. Call number: STC 1167 copy 1; displayed p. 266 and LUNA Digital Image.
- LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. William F. Friedman. “KNOWLEDGE IS POWER.” Aurora, Ill., ca. January 1918.
Disks and Volvelles (case 10 and wall panel)
The cipher disc may be the most iconic image in the history of cryptography. And for good reason: it puts a simple but powerful system of alphanumeric substitution into the palm of one's hand. In portable form, it was particularly well-suited for use in the field. Within the covers of the period's books, it became one of the primary applications of the new technology called the volvelle, where one circle (often featuring a pointing hand) could be turned on top of another, with each turn of the disk presenting a new cipher alphabet.
Friedman's friend, the classicist and cryptanalyst Charles J. Mendelsohn, considered Giambattista della Porta the outstanding cryptographer of the Renaissance. He had a particularly solid grasp of the use of cipher disks, explaining how they can be converted into tables and vice versa. His books featured some of the period's most ornate volvelles.
Items Included
Case 10
- Jacopo Silvestri. Opus novum. Rome: Marcello Silber, 1526. Call number: Z103 .S5 1526 Cage; displayed fol. 6v.
- Giambattista della Porta. De furtivis literarum notis. London: John Wolfe, 1591. Call number: STC 20118a; displayed p. 72–73 and LUNA Digital Image.
- Johannes Trithemius. Polygraphie et universelle escriture caballistique. Paris: Jacques Kerver, 1625. Call number: Z103.T7 P6 F7 1625 Cage; displayed p. 328.
Wall Panel
- Leon Battista Alberti. Opuscoli morali. Venice: Francesco di Franceschi, 1568. Call number: PQ4562 .A6 1568 Cage and LUNA Digital Image.
Grilles (case 11)
The popular scientist Girolamo Cardano was credited with an invention that is still in use today. In the so-called "Cardan grille" a sheet with irregular holes cut in it is laid over a blank page and the intended message is written in the spaces. The sheet is then removed and the rest of the spaces are filled in with innocent—or even misleading—text. When the recipient lays the same grid over the letter in the same position, the hidden message is revealed.
Della Porta’s popular treatise on secret writing includes clear instructions for using a grille—or a membrane, as he describes it—with windows and gaps (fenestras et vacua). To make sure that the recipient knows where to place the overlay, four points should be drawn to mark the edges.
Items Included
- Girolamo Cardano. Hieronymi Cardani Mediolanensis medici De rerum uarietate libri XVII. Basel: Heinrich Petri, 1557. Call number: 156- 884f; displayed title page.
- Giambattista della Porta. De occultis literarum notis seu Artis animi sensa occulte alijs significandi. Montbéliard: Jacques Foillet and Lazarus Zetzner, 1593. Call number: 173- 568.1q; displayed p. 134.
- LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. William F. Friedman and Elizebeth S. Friedman. Cryptographic Christmas Card for 1928.
- LOAN courtesy of the Massachusetts Historical Society. John Clotworthy, viscount Masereene. Autograph letter to John Winthrop, Jr., with grille. Dublin, 6 March 1634/35. Collection guide to the Winthrop Family Papers, 1537–1990.
Say It with Flowers (case 12)
Friedman and his team at Riverbank were always on the lookout for ways to apply Renaissance codes to modern life. In 1920 they published an article for the Florists' Review on the famous trade slogan, "Say It With Flowers," suggesting that carefully designed bouquets could not only express general sentiments (such as love or sympathy) but also carry hidden messages. They provided an example from a seventeenth century German cryptography manual using a floral wreath and alphabetical key.
Items Included
- FACSIMILE from the Bacon cipher collection. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox and Tilden Foundations. Cora Jensen [and William F. Friedman]. "‘Saying It’ in Cipher." Florists’ Review, 1920. NYPL Call number: MssCol 176.
- LOAN courtesy of the Library of Congress. Johann Balthasar Friderici. Cryptographia. Hamburg: Georg Rebenlein, 1685. LOC Call number: Z103.5 .F75 1685 Fabyan Coll.
- LOAN courtesy of the Library of Congress. Loose-leaf note from Friedman’s team at Riverbank in Johann Balthasar Friderici. Cryptographia. Hamburg: Georg Rebenlein, 1685. LOC Call number: Z103.5 .F75 1685 Fabyan Coll.
- FACSIMILE from the Bacon cipher collection. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox and Tilden Foundations. [Cora Jensen and William F. Friedman]. “‘Saying It’ in Cipher.” Typescript, 1920. NYPL Call number: MssCol 176.
Music (case 13)
Music was another signifying system that could be used both to convey and to cover secret messages, with particular notes standing in for the different letters in the alphabet. The systems shown in this case made it possible for musical compositions to speak to people even when they did not contain words.
As in other examples, Friedman used the sheet music (arranged for solo mandolin) for Stephen Foster's famous song, "My Old Kentucky Home, Good Night" to show how, using Bacon's biliteral cipher, anything can be made to signify anything. By making notches in the stems of some notes and leaving others whole, he has turned the music into a sequence of a's and b's that read "Enemy advancing right / We march at daybreak."
Items Included
- FACSIMILE (adapted with message deciphered) from the Bacon cipher collection. Manuscripts and Archives Division, The New York Public Library, Astor, Lenox and Tilden Foundations. William F. Friedman. "My Old Kentucky Home, Good Night". Modified sheet music, 1916. NYPL Call number: MssCol 176.
- John Wilkins. Mercury: or, The secret and swift messenger. London: for Richard Baldwin, 1694. Call number: W2203; displayed p. 144–45 .
- LOAN courtesy of the Library of Congress. Johannes Balthasar Friderici. Cryptographia. Hamburg: Georg Rebenlein, 1685. LOC Call number: Z103.5 .F75 1685 Fabyan Coll.
- Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. Cryptomenytices et cryptographiae libri IX. Lüneburg: Johann and Heinrich Stem, 1623. Call number: Z103 .A9 1624 Cage; displayed p. 324–35.
Steganography (case 14)
The best way to keep a secret message secure is to hide the very fact that there is a secret message at all. Alongside the development of cryptography (whereby a message is scrambled using transposition or substitution), there has been a parallel field called steganography (in which messages are kept intact but hidden within an innocent cover). We have already seen several examples of this art, including invisible ink, floral codes, and modified sheet music, and this case introduces several methods for hiding writing within pictures.
Items Included
- Johannes Balthasar Friderici. Cryptographia. Hamburg: Georg Rebenlein, 1685. Call number: 166- 900q; displayed loose leaf opp. p. 217.
- LOAN courtesy of the Library of Congress. Blaise de Vigenère. Traicté des chiffres, ou, Secretes manieres d’escrire. Paris: Abel L’Angelier, 1587. LOC Call number: Z103.5 .V54 1587 Fabyan Coll
- Gustavus Selenus [pseudonym for August II, Duke of Braunschweig-Lüneburg-Wolfenbüttel]. Cryptomenytices et cryptographiae libri IX. Lüneburg: Johann and Heinrich Stem, 1624. Call number: Z103 .A9 1623 Cage; displayed p. 340–41.
Enigmas and Machines (zone 3)
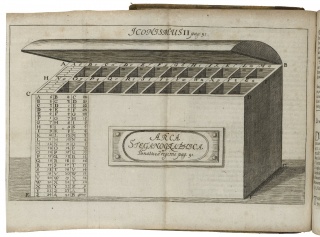
- Bacon was, in fact, the inventor of the binary code that forms the basis of modern electronic digital computers.
- —William F. Friedman, Six Lectures on Cryptology (1959–61)
Cryptography Before the Computer (case 15)
Well before the advent of digital technology, those working in the field of cryptography turned to machines to make the production and transmission of secret messages easier, faster, and more secure. Many of these devices (from Alberti's introduction of the cipher disk in the 1460s to the rotor-based SIGABA machine invented by Friedman and his colleagues in the 1930s) used single or multiple wheels to systematize the scrambling of letters. Friedman lived just long enough to see his field transformed by the introduction of computers—and to claim that "Bacon was the inventor of the binary code" on which they depend.
SIGABA Machine
In the 1930s, William Friedman and Frank Rowlett (Army) and Commander Laurance Safford (Navy) invented an improved cipher machine for use by both forces: it was known as SIGABA in the Army and ECM (for Electric Code Machine) Mark II in the Navy. The basic operation was similar to the Enigma machine used by the Germans, but the Americans increased the number of rotors and improved the randomization of their movement. Unlike the Enigma, the SIGABA was never broken: it remained in use through the 1950s and was not declassified until 2000.
Cyclologic Cryptographic Machine
In 1666, Samuel Mordland published A new method of cryptography, considered today one of the rarest books in the field. This short treatise on cryptography drew on his work intercepting and decoding coded correspondence during the English Civil War (1642–51). It culminates in a “Cyclologic Cryptographic Machine,” illustrated on the book’s final page: using a series of cipher-wheels turned by a stylus, it was closely related to the mechanical adding machine he invented the same year.
Items Included
- LOAN courtesy of the National Cryptologic Museum, NSA. William F. Friedman. SIGABA machine.
- FACSIMILE from the National Cryptologic Museum, NSA. US patent 6,175,625. January 16, 2001. Digital Copy of Patent
- Samuel Morland. A new method of cryptography. London: 1666. Call number: M2781A; displayed p. 12 and LUNA Digital Image.
- LOAN courtesy of the Preservation Partners of the Fox Valley and Kane County Forest Preserve District. Wheatstone-Plett Cipher Device. From George Fabyan’s collection at Riverbank Laboratories.
Kircher's Cryptographic Machines (case 16)
The last of the great Renaissance polymaths, the Jesuit scholar Athanasius Kircher published books on the secrets of the universe ranging from the subterranean to the super-celestial and from the ancient past to the distant future. He loved letters and numbers in equal measure, and dreamed up endless devices to help them work and play together.
Items Included
- Gaspar Schott. Schola steganographica. Nuremberg: Heirs of Johann and Wolfgang Endter, 1680. Call number: 170- 941q; displayed opp. p. 91.
- Athanasius Kircher. Magnes sive De arte magnetic. Rome: Biaggio Diversin, Zenobio Masotti, and Vitale Mascardi, 1654. Call number: 166- 834f; displayed p. 290–91.
The Voynich Mystery (case 17)
In 1912, a rare book dealer named Wilfrid M. Voynich acquired a cache of manuscripts from a Jesuit college near Rome. Among them was the strange codex that now bears his name, a heavily illustrated text on vellum, carefully written by an unknown author in an elaborate script or symbol system that has never been deciphered. The great Chaucerian (and World War I code-breaker) John M. Manly, one of the first scholars to examine the volume, described it as "the most mysterious manuscript in the world," and a full century after it resurfaced we still know surprisingly little about it. The cracking of the Voynich Code—if that is what it is—has long been a holy grail for students of cryptography. Research from other angles (including the history of botanical illustration and the use of computers to analyze patterns) continues to generate fresh theories that keep the manuscript in the news. We hope that this exhibition will provide new information and inspiration for the amateur and professional scholars who fall under its spell.
Historian René Zandbergen's website provides more detailed information on this curious manuscript.
Items Included
- LOAN courtesy of the Beinecke Library, Yale University. The Voynich Manuscript. (ca. 1410–30). Yale Call number: Beinecke MS 408 and Beinecke Digital Manuscript.
The Friedmans and the Folger (case 18)
The Friedmans' final home was a nondescript Washington rowhouse near the corner of 2nd and C Streets SE. This location put them at the heart of the government community on Capitol Hill and gave them easy access to both the Library of Congress and the Folger Shakespeare Library. Their definitive debunking of anti-Stratfordian ciphers found an enthusiastic home here at the Folger: the couple's original manuscript won the Library's book prize and was deposited in its archive. Folders from the Friedmans’ post-retirement research are filled with the familiar green call-slips still used for Folger books, and William's 1962 article on "Shakespeare, Secret Intelligence, and Statecraft" identified him only as "Reader, Folger Shakespeare Library."
Items Included
- William F. Friedman and Elizebeth S. Friedman. The cryptologist looks at Shakespeare. Manuscript. Typescript, 1954. Call number: Y.d.76; displayed chapters 1–6 stacked, title page on top.
- William F. Friedman and Elizebeth S. Friedman. The Shakespearean Ciphers Examined. Cambridge: Cambridge University Press, 1957. Call number: PR2937 .F7 1957 Copy 2 Cage; displayed front endleaf 1r.
- LOAN courtesy of the George C. Marshall Foundation, Lexington, VA. Washington Post, April 3, 1955
The Friedmans and the Voynich Manucript (case 19)
After the Bacon-Shakespeare controversy, the Friedmans' favorite extracurricular project was the Voynich Manuscript. As his country's leading expert on secret writing systems, William Friedman was quickly enlisted to solve the Voynich mystery. During three different periods of sustained study (in the 1920s, 40s, and 60s), Friedman threw all available resources at the problem, including some of the earliest use of computer-assisted text analysis. But the manuscript stubbornly refused to yield its secrets to Friedman (as it had to Kircher when he was consulted in 1666), and he died with only vague theories and not a single line of deciphered text.
Friedman on the Voynich Solution
In a typical display of cryptic wit, Friedman recorded his final theory about the Voynich Manuscript in the form of an anagram, and embedded it into the final paragraph of his 1959 article on anagrams in Chaucer—rearranging the letters by hand and filing the cut-out tiles in his archive. The solution was kept in a sealed envelope and only published after his death:
- “The Voynich MS was an early attempt to construct an artificial or universal language of the a priori type. —Friedman.”
Friedman felt, in the end, that there was no code to be broken but rather an entirely invented language whose rules we do not yet know.
Items Included
- LOAN courtesy of the George C. Marshall Foundation. William F. Friedman and the Voynich Manuscript Study Group. Voynich character frequency tables, ca. 1944. Collection of William F. Friedman Papers.
- LOAN courtesy of the George C. Marshall Foundation. William F. Friedman and the Voynich Manuscript Study Group. Agreed alphabet for transcription of Voynich characters. June 13, 1944
- LOAN courtesy of the George C. Marshall Foundation. Lexington, VA. RCA Computer run of characters from the Voynich Manuscript, ca. 1962
Puzzling Pages (case 20)

People who have the qualities of mind needed to make and break codes often delight in puzzles. There has long been a close affinity between cryptanalysts and crossword puzzles, and Friedman was one of many who got their first introduction to the field through Edgar Allan Poe—who wrote a regular newspaper column in which he solved ciphers sent in to him by readers and whose famous story "The Gold Bug" played a major role in popularizing cryptograms.
Items Included
- Athanasius Kircher. Polygraphia nova et universalis ex combinatoria arte detecta. Rome: Lazzari Varese, 1663. Call number: Folio P361 .K5 1663 Cage; displayed p. 23.
- Henry Clay Folger and Emily C. J. Folger. Solution to "Shakespearean Enigma" crossword. New York Herald Tribune, March 15, 1925. Call number: Y.d.1009; displayed 2b and LUNA Digital Image.
- LOAN courtesy of the George C. Marshall Foundation, William F. Friedman and Elizebeth S. Friedman. Cryptographic dinner menu, May 15, 1929.